Why prevent external access to Teams?
In some instances, Teams and SharePoint team sites may contain information that is very definitely only intended for internal use. To limit data loss and accidental oversharing, Microsoft 365 governance best practice is to prevent team owners and members from adding external users (outside the organizational tenant).
What is needed to prevent external access?
Two configuration settings in tandem achieve the lockdown state described above:
- The AllowToAddGuests setting on Microsoft 365 groups
- The External Sharing setting on a SharePoint site
SProbot enables you to automate the enforcement of these settings to specific Teams and SharePoint sites by enabling a rule to be configured on a pipeline, and then automatically applying it to all workspaces requested via the pipeline.
Define the setting
In the Governance Rules step of a pipeline, use the Prevent guest access checkbox to enable lockdown.
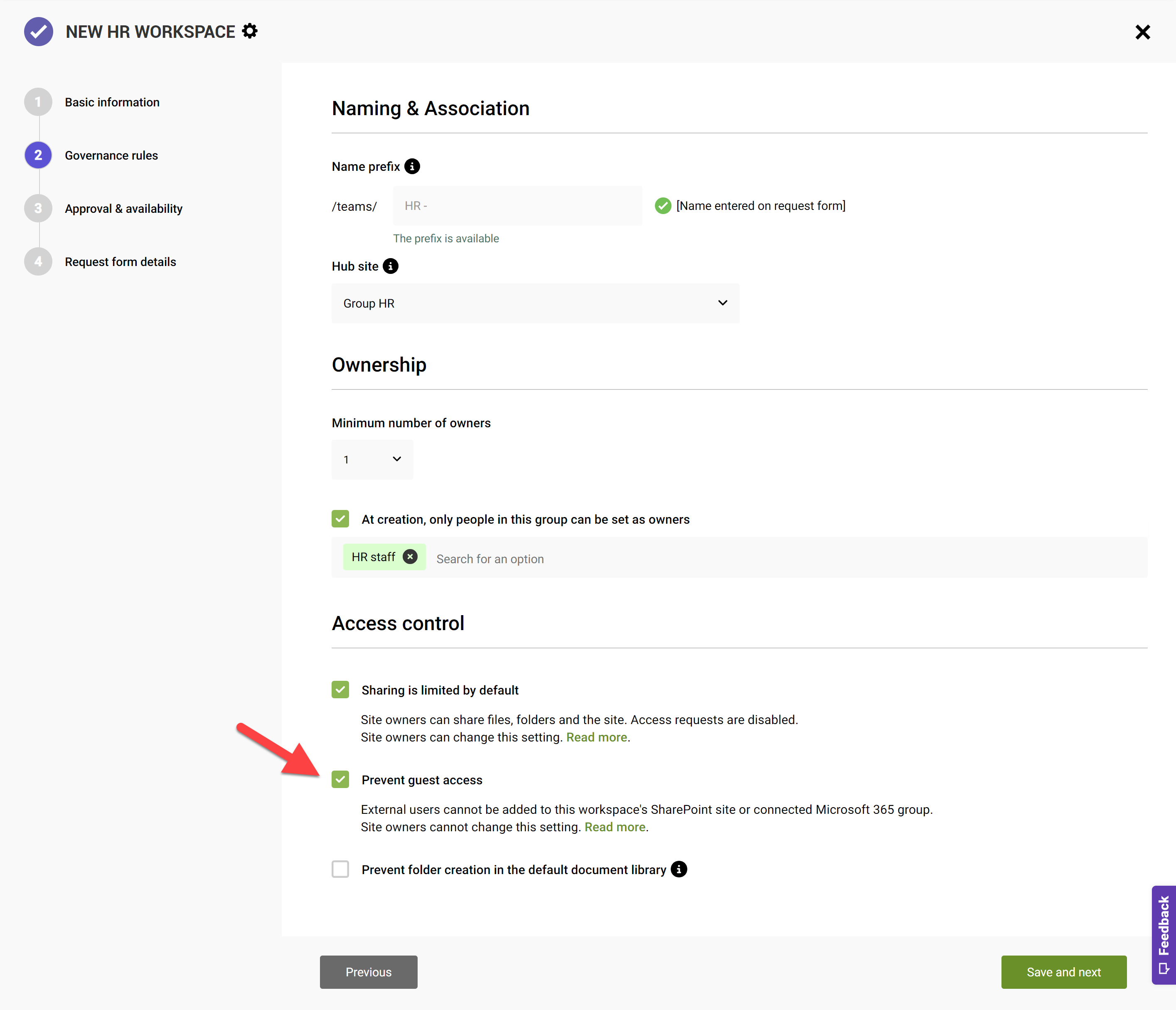
Effects of the setting
With this setting applied, group owners will not be able to add external/guest user to their groups. When searching for an external user, they will simply not be found.

Considerations
It is important to remember that this setting is in fact two separate settings, one applied to the Microsoft 365 group, the other to the associated team site. This means that it effects both Teams and SharePoint, so serves as an overarching lockdown for both the Teams app and its Files (which reside in SharePoint). Group/site owners cannot change this setting without administrator assistance, so if in future a specific team should not be locked down anymore, both the group and site settings will need to be manually updated.

More guides

Use the sites with large files review to identify sites and teams which contain large files which can be cleaned up to increase available storage
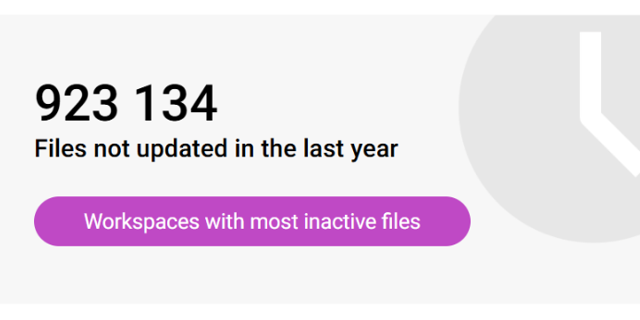
Use the sites with inactive files review to identify sites and teams which have a large percentage of inactive files
Use the Reviews tools to proactively identify and resolve issues which may affect storage and security on your tenant