Managing how content is shared in SharePoint Online is crucial for balancing collaboration and security. The more secure content is, the more friction there is which interferes with collaboration, and vice versa.
Microsoft 365 administrators can control external sharing settings at both the tenant (organization) level and the site level. By fine-tuning these settings – from allowing broad access to locking down content – you ensure that users can share with the right people without exposing data to risk.
In this article, we’ll explain SharePoint Online’s sharing configuration options (from most permissive to least permissive), and show step-by-step how to adjust them at both the tenant and site levels (using the SharePoint admin center and PnP PowerShell). We’ll also highlight best practices for choosing the appropriate sharing level for your organization.
Understanding SharePoint Online Sharing Levels
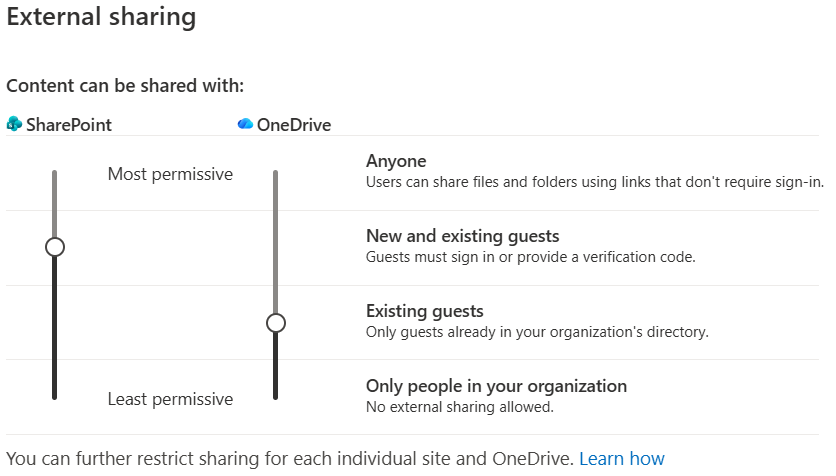
SharePoint Online offers four main external sharing levels (also applicable to OneDrive) that range from fully open to completely restricted.
- Tenant-level settings define the maximum allowed sharing capability across your entire organization.
- Site-level settings can be used to further restrict specific sites (they cannot be more permissive than the tenant setting).
The default tenant setting is often the most permissive (“Anyone”), but many organizations choose a more restrictive default for security.
❗Important: Each SharePoint site’s sharing setting must be the same or more restrictive than the tenant’s. For instance, if the tenant allows “Anyone,” a site can limit sharing to “New and existing guests,” but not vice versa. Set the tenant-level sharing to match the requirements of the most permissive department/area in your organisation, then restrict sharing further on sensitive sites if needed.
External Sharing Levels (Most Permissive → Least Permissive):
Anyone (Anonymous Links)
This sharing option allows users to share files and folders with anyone by generating an anonymous link. Recipients of this link do not need to sign in or have any form of authentication to access the shared content.
The main advantage of this approach is that it provides the easiest and most seamless sharing experience for both internal and external users. However, there are important security implications to consider. Because links can be forwarded freely, the content may be accessed by unintended recipients, and there is no way to track exactly who views or interacts with the files or folders.
For these reasons, it is best to reserve “Anyone” links for sharing low-risk content. To enhance security when using this sharing level, consider setting expiration dates on anonymous links and applying view-only permissions where appropriate.
New and existing guests
With the "New and existing guests" sharing setting, files, folders, and sites can be shared with external users who are required to authenticate themselves. This means that anyone accessing the shared content must sign in using either a Microsoft account, an organizational account, or by entering a one-time code provided during the sharing process.
The primary implication of this option is that while external sharing is enabled, anonymous access is not permitted. Every external user who receives access is identifiable, as their authentication is mandatory. As a result, organizations maintain oversight and control over who can view or interact with shared content.
This sharing level is broadly recommended for many organizations as a default setting. It strikes a balance between facilitating collaboration with external partners or customers and maintaining a secure environment where all external access is logged and controlled.
Existing guests only
This sharing option permits sharing content exclusively with external users who are already present in your organization’s directory as pre-existing guest accounts. New external users cannot be invited directly; instead, an administrator must add them in Microsoft Entra before you can share with them.
The primary implication of this setting is that it enforces tightly controlled external sharing. It is particularly suitable when there is a need to strictly limit external collaboration to trusted, known entities. While this approach increases security by blocking ad-hoc invitations and ensuring only pre-provisioned guests can access content, it also introduces additional steps for new external sharing, as someone must manually add the guest in advance.
Only people in your organization
This sharing setting is the most restrictive option available for content sharing. When enabled, external sharing is completely disabled, meaning that documents, files, and folders can only be accessed by licensed users within your organization's tenant. All access previously granted to external guest users is immediately revoked. However, if external sharing is re-enabled at a later time, access for prior guest users can be restored.
The primary implication of this approach is maximum security. It is best suited for scenarios involving highly confidential or sensitive information that must remain strictly internal. While this restriction ensures that no data is inadvertently exposed outside the organization, it is important to consider that it may also hinder collaboration with external partners, clients, or stakeholders, as all sharing with users outside your organization is blocked.
Adjusting Sharing Settings at the Tenant (Organization) Level
Tenant-level external sharing settings apply to all SharePoint sites in your organization, and serve as the upper limit for OneDrive sharing as well. Follow these steps to review or change the sharing level for the entire tenant:
Via the SharePoint Admin Center:
To configure the tenant sharing policy in the SharePoint admin center, follow these simple steps:
- Navigate to Policies > Sharing. This will display the organization-wide sharing settings for SharePoint and OneDrive.
- In the External sharing section, select the level of sharing for SharePoint (and optionally for OneDrive).
- Scroll to the bottom of the Sharing page and select Save.
Once this change is saved, all sites in SharePoint Online will be constrained to this setting or more restrictive. For instance, if you moved from “Anyone” to “New and existing guests” at the tenant level, any previously shared anonymous guest links will stop working (within about an hour) because anonymous access is now turned off.
*Note - OneDrive will never be more permissive than SharePoint but it can be less permissive.
Via PnP PowerShell:
To configure the tenant sharing policy to the most restrictive in PowerShell, connect to your SharePoint admin URL (https:example-admin.sharepoint.com) and use the following command:
Set-PnPTenant -SharingCapability Disabled
The options for sharing are as follows:
- ExternalUserAndGuestSharing – Equivalent to “Anyone”
- ExternalUserSharingOnly - Equivalent to "New and existing guests”
- ExistingExternalUserSharingOnly - Equivalent to "Existing guests”
- Disabled – Equivalent to “Only people in your organization”
Changing the tenant SharingCapability via PowerShell has the same effect as using the admin center slider. Be cautious – lowering permissiveness (e.g., to Disabled) will immediately cut off existing external access across all sites (any external links or guest access will stop working).
Adjusting Sharing Settings at the Site Level
Sometimes you’ll want stricter sharing settings on a particular SharePoint site (for sensitive content) without locking down the entire tenant. As long as the tenant allows a given level, you can configure an individual site to an equal or more restrictive level. For example, if your tenant setting is “Anyone,” you might set a particular site to “Existing guests only” or even “Only people in your organization.” Here’s how:
Via SharePoint Admin Center (per site):
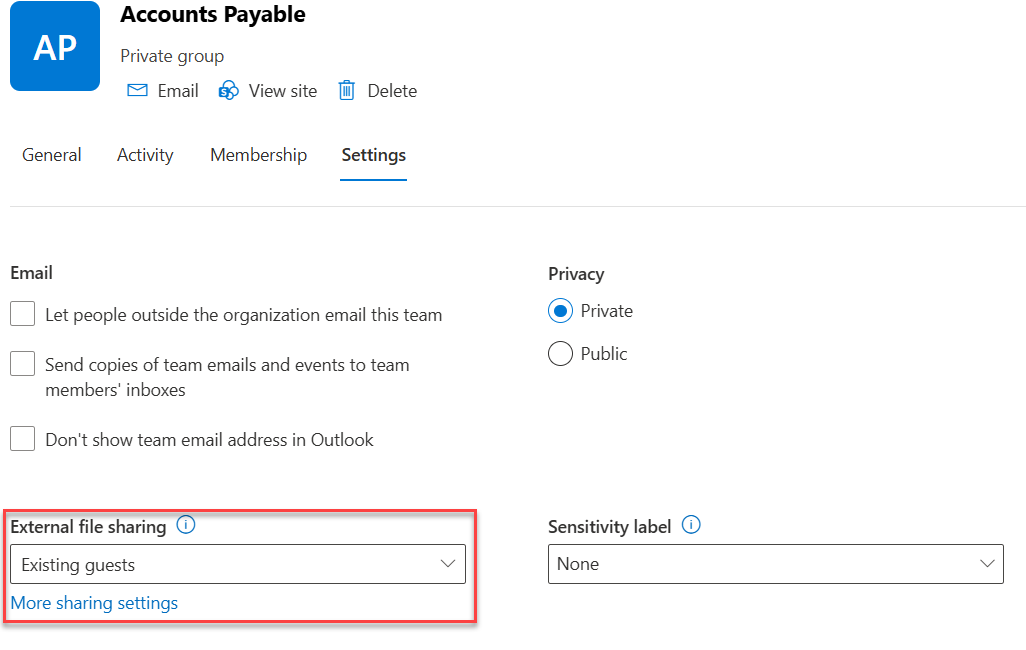
To configure the sharing settings of individual sites from the SharePoint admin center, follow these simple steps:
- Go to Sites > Active sites and open the detail panel for the selected site.
- In the detail panel, select the Settings tab.
- Under the External file sharing section, choose the preferred sharing setting.
- Save to update the setting for the site.
Via PnP PowerShell:
To configure an individual site’s sharing policy to the most restrictive in PowerShell, connect to your SharePoint admin URL (https:example-admin.sharepoint.com) and use the following command:
Set-PnPTenantSite -Identity <Site URL> -SharingCapability Disabled
The same SharingCapability options are available as on the tenant level, as long as that level is not more permissive than the tenant level policy.
Tip - You can verify a site’s current sharing setting with Get-PnPTenantSite -Identity <SiteURL> | Select SharingCapability
Best Practices for Choosing Sharing Levels
Choosing the appropriate sharing configuration requires balancing security needs against business productivity. Here are some best-practice guidelines for Microsoft 365 admins:
- Least Privilege Principle – Always start with the least permissive setting that meets requirements, especially for new deployments. It’s easier to loosen restrictions later than to revoke access that was too open. If unsure, avoid “Anyone” and opt for requiring sign-in (guests).
- Default Link Settings – Along with external sharing levels, configure the default sharing link type to prevent accidental exposure. For example, if you disallow Anyone externally, set the default link to “People in your organization” or “Specific people” to encourage safer sharing. Users can still choose a broader link if needed (assuming policy allows) but won’t do so by mistake.
- Monitor and Adjust – Regularly review sharing reports or use tools as described in our How to manage sharing links in SharePoint article to see how your content is being shared. If you find sites with anonymous links that shouldn’t have them, tighten those settings. Also, as your organization’s needs change, revisit the tenant setting – for instance, if partner collaboration increases, you might enable external sharing (with guests) if it was previously off.
- Educate Users - Ensure that your users (especially site owners) understand what each sharing option means. They should know, for example, that if a link is created with “Anyone,” it can be forwarded to outsiders. Encourage use of more restrictive links for sensitive info, and possibly enforce through training or governance policies.
By carefully adjusting the sharing policy at both the tenant and site level, you can achieve a secure-yet-collaborative environment. Start with a sensible default (in most cases, allowing external sharing with authenticated guests) and then apply stricter controls on the sites that need them. Regularly auditing and updating these settings will help maintain the right balance over time – keeping your organization’s data safe while still enabling teamwork with the people who need access.














